AI agents are superpowers for your teams, but they're also shadow risks multiplying across your business.
Noma's Agentic Risk Map shows you every agent, every tool connection, and every risk before one rogue action or malicious prompt cascades across your infrastructure.
The Challenge
Agents multiply across SaaS, cloud, and local environments, from no-code platforms to custom built agents. Security teams can't see them. Can't track them. Can't control the sprawl.
Agents connect to tools through MCP, communicate with other agents (A2A), tap into knowledge sources and channels, and can trigger destructive actions. A single compromise can ripple through entire ecosystems.
Compromised agents don't wait for approval. They autonomously execute malicious workflows, trigger downstream agents, and compound damage across your infrastructure, all in seconds, not hours.
Security teams block agent deployments because they can't assess the risk. Business teams deploy agents anyway because they can't wait. The result? Innovation happens in the shadows, and security has no visibility until something breaks.
Noma’s Solution
Introducing Noma’s Agentic Risk Map.
The Industry’s first solution to visualize agent sprawl, reveal the blast radius and provide full control of the Agent attack surface.
Complete visibility and management of Agentic AI
Noma ARM delivers the first security solution built specifically for autonomous AI agents combining Discovery, Posture Management, and Runtime Protection into one comprehensive tool to visualize and control the Agent Blast Radius.
Zero blind spots. Complete Agent control.
Visualize every Agent
Finally, a visual map that makes agent sprawl impossible to hide. Discover, catalog and visualize every agent across your infrastructure.
Expose the blast radius
Analyze each agent’s connections, tools, identities, and knowledge sources to uncover cascading risk scenarios. Intercept dangerous combinations before deployment.
Visualize every Agent
Continuously monitor agent behavior to detect prompt injections, tool abuse, risky actions, and data leakage. Instantly alert, isolate, or revoke access to contain threats.
Secure the agentic future
Adopt agents confidently with end-to-end protection across discovery, build, and runtime. Accelerate innovation while maintaining full visibility and control at every stage.
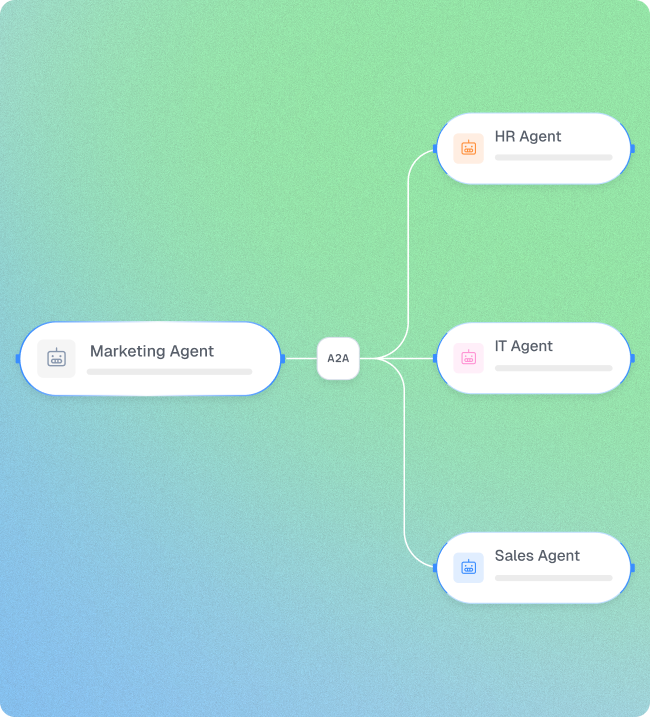



Visualize every Agent
Finally, a visual map that makes agent sprawl impossible to hide. Discover, catalog and visualize every agent across your infrastructure.
Expose the blast radius
Analyze each agent’s connections, tools, identities, and knowledge sources to uncover cascading risk scenarios. Intercept dangerous combinations before deployment.
Defend in real time
Continuously monitor agent behavior to detect prompt injections, tool abuse, risky actions, and data leakage. Instantly alert, isolate, or revoke access to contain threats.
Secure the agentic future
Adopt agents confidently with end-to-end protection across discovery, build, and runtime. Accelerate innovation while maintaining full visibility and control at every stage.
Zero blind spots. Complete Agent control.
Visualize every Agent
Finally, a visual map that makes agent sprawl impossible to hide. Discover, catalog and visualize every agent across your infrastructure.
Expose the blast radius
Analyze each agent’s connections, tools, identities, and knowledge sources to uncover cascading risk scenarios. Intercept dangerous combinations before deployment.
Defend in real time
Continuously monitor agent behavior to detect prompt injections, tool abuse, risky actions, and data leakage. Instantly alert, isolate, or revoke access to contain threats.
Secure the agentic future
Adopt agents confidently with end-to-end protection across discovery, build, and runtime. Accelerate innovation while maintaining full visibility and control at every stage.
Why this
matters now
AI agents are becoming the operational backbone of enterprise, but unlike traditional AI, they act autonomously with destructive capabilities. One compromised agent can access multiple systems, trigger automated workflows, and cascade damage across your entire infrastructure, amplifying risk 100x.
Excessive Autonomy
Unrestricted decision making combined with access to sensitive data and systems.
Over Permissive Access
Agents accumulate credentials, turning a single compromise into lateral movement across your entire environment.
Excessive Functionality
Expanded capabilities can be abused through malicious inputs or compromised components.
Blast
Radius
Compromised agents trigger chain reactions across systems, turning isolated issues into organization-wide incidents.
Turn hidden Agentic Risks
into visible Insights.
Gain the clarity you need to detect, prioritize, and control agentic threats before they spread