The Noma Agentic Risk Map Delivers Complete AI Agent Visibility and Control
From Superpower to Shadow Risk
AI agents give your business many superpowers. Developers use Cursor to write code at machine speed. Knowledge workers delegate complex tasks to ChatGPT Agents. Business teams build custom automation through low-code platforms like Microsoft Copilot Studio and Salesforce Agentforce. Engineering teams deploy sophisticated agent systems in production across cloud infrastructure and internal applications. Anyone can now spin up autonomous helpers that dramatically boost productivity and amplify organizational value.
But this transformative power comes with a critical challenge. Unlike traditional LLM-based applications, AI agents act autonomously across your entire digital ecosystem, connecting to databases, sending emails, executing code, and making decisions that ripple through your organization. They’re proliferating everywhere simultaneously, and security teams have lost visibility and control over what these agents can access, who can trigger them, and how they interact with each other. When agents invoke other agents, access tools dynamically, and operate across organizational boundaries, existing security controls cannot monitor or govern this interconnected web of autonomous activity. As a result, security teams have lost control over what is rapidly becoming the operational backbone of their organizations.
The Complex AI Agent Threat Landscape
Beyond their autonomy, agentic systems introduce a new layer of complexity. Each agent often carries its own identity, permissions, and access footprint, interacting with organizational assets in ways that resemble human users but operate at machine speed. They tap into specialized tools and APIs, coordinate with other agents through agent-to-agent (A2A) protocols, and can even leverage Model Context Protocol (MCP) to dynamically discover and orchestrate new capabilities. In multi-agent environments, these interactions form intricate webs of delegated authority, data flows, and chained decisions that can evolve in real time. What was once a linear application stack is now a dynamic mesh of autonomous entities, each capable of triggering actions, spawning new processes, or influencing other agents. This creates unprecedented operational power but also amplifies the potential blast radius of a single weak link.
Compounding this challenge, agents now proliferate across every layer of the enterprise: from SaaS platforms and low-code/no-code environments like Microsoft Copilot Studio and Salesforce Agentforce, to production systems running on cloud infrastructure and internal applications, to individual employee endpoints where developers use Cursor and knowledge workers rely on ChatGPT agents and AI assistants. Each deployment environment introduces distinct security considerations, governance requirements, and visibility gaps that traditional security tools were never designed to address.
As enterprises rapidly embrace agentic AI and agents become the new operational backbone of large organizations, the security paradigm must fundamentally shift from monitoring isolated systems to mapping the complex web of agent interactions, tool access privileges, and cascading data flows that now define AI risk at the organizational level. Security teams are operating blind in this new agentic landscape, making this a critical moment to establish comprehensive visibility and control before agent sprawl outpaces security measures entirely.
Real-World Agentic AI Blast Radius Scenarios

The fundamental challenge isn’t just that individual agents are powerful, it’s that organizations have lost visibility and have no control over the sprawling maze of agent-to-agent connections, tool relationships, and cross-system permissions that now define their infrastructure. Agents connect to other agents, which connect to tools, which trigger additional agents, which access more tools, creating a tangled web of delegated authority where no single team understands what can access what, who can trigger whom, or where a compromised interaction might lead. Traditional security controls designed for linear application flows simply cannot map, monitor, or contain risks in this agent maze where relationships multiply faster than governance processes can document them.
A Common AI Agent Risk Scenario
A customer service AI agent receives a support request through a chat interface. This agent has been granted broad permissions to “resolve customer issues efficiently,” which in practice means it can:
- Execute code to query and update customer records across multiple databases
- Process refunds and financial transactions without human approval thresholds
- Send emails directly to customers using official company templates
- Access and transmit sensitive customer data including payment information and personal details
- Trigger downstream agents for order fulfillment, inventory management, and billing adjustments
- Modify account settings and permissions based on customer requests
A single manipulated prompt or indirect injection through a customer complaint can cascade into:
- Unauthorized code execution that extracts customer databases or modifies backend systems
- Mass data exfiltration where sensitive customer information is sent to external endpoints disguised as legitimate API calls
- Financial fraud through automated refund processing to attacker-controlled accounts
- Email-based attacks where the agent sends phishing emails or malicious attachments to customers using trusted company infrastructure
- Agent-to-agent exploitation where the compromised customer service agent triggers payment processing agents, inventory agents, and notification agents, each amplifying the damage across different business functions
- Persistent access as the agent creates new user accounts, modifies permissions, or establishes backdoors for future exploitation
This cascading effect starts when one compromised agent interaction ripples outward through interconnected systems, triggering other agents and automated workflows that affect customers, employees, and critical business operations, and represents the core of the blast radius problem. When AI agents can autonomously invoke other agents, access destructive capabilities, and operate across organizational boundaries without centralized oversight, a single vulnerability doesn’t just compromise one system, it potentially compromises everything that agent maze touches.
The Noma Agentic Risk Map Visualizes the Agentic AI Attack Surface
The just-released Noma Agentic Risk Map addresses this rapidly growing security challenge through a systematic approach built on three core principles: AI agent discovery, posture management, secure design, and runtime monitoring. This isn’t just another monitoring tool, it’s a complete agentic AI security platform for visibility and control, and designed specifically for the enterprise AI agent security requirements of today and tomorrow.
Discovery: Mapping the AI Agent Ecosystem

The foundation of effective AI agent security is visibility. The Noma Security platform discovers and catalogs agents and tools (e.g MCP servers) across the entire infrastructure, including:
- SaaS no code / low code – Microsoft Copilot Studio, ServiceNow, Salesforce Agentforce, Google Agentspace
- Cloud service providers offering no-code to pro-code agent builder capabilities – Azure AI Foundry, Google Vertex AI, AWS Bedrock AgentCore
- Agentic SDKs – LangChain, CrewAI, Google Agent Development Kit
- Coding agents – Cursor, GitHub Copilot, Claude Code, Codex
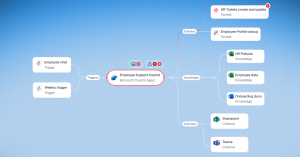
Noma Discovery feeds the Noma Agentic Risk Map to create a comprehensive and contextualized visualization that operates across two critical dimensions:
- Comprehensive agent connectivity mapping reveals the complete network of agent relationships. Like a detailed map providing a lens on each direction you could take, it shows every connection, split, and pathway agents use to access tools and communicate with each other. This includes mapping agent connections to various tools and Model Context Protocol (MCP) servers, identifying agent-to-agent (A2A) communication paths, and tracking how agents access different capabilities. Think of it as an illuminating guide into how agents find creative ways to reach tools that can be exploited by attackers or lead to unintended, potentially destructive, consequences.
- Deep context provides insights into detailed relationships needed to understand risk at every node. For each agent, tool, and connection point, we gather critical intelligence: how the agent is scoped and guided, what data and knowledge it has, what actions and tools it can trigger, and the agent’s identity. This combination of connectivity mapping and deep object analysis provides the complete context security teams need to make informed decisions.
Posture: Identifying Toxic Risk Combinations
With complete visibility established, the Noma Security platform uses context to analyze agent mappings and context to identify dangerous risk combinations:
- An agent with code execution capabilities connected to a public communication channel is a perfect vector for remote code execution
- An agent authorized to send external emails without human approval, enabling data exfiltration or business email compromise
- An agent performing destructive actions (like database deletions) while processing context from untrusted public sources that are vulnerable to indirect prompt injection attacks
These risk scenarios only become apparent when you can see the full picture of agent capabilities, connections, and access patterns. Noma Security agentic AI security posture analysis transforms complex technical relationships into clear risk assessments that security teams can act upon. Crucially, we intercept these risks at the source during the build phase before agents ever reach production.
When developers build agents, they start in a “disabled” state and must be explicitly “enabled” for deployment. This creates a critical security gate where our platform runs comprehensive risk assessments before activation. We analyze the agent’s intended capabilities, planned connections, and configured permissions to identify dangerous combinations before they can cause damage. This build-time intervention prevents risky agents from entering production environments, transforming agent security from reactive incident response to proactive risk prevention.
Runtime Monitoring: Real-Time Threat Detection and Response
Security posture is only as good as your ability to detect and respond to active threats. Noma Security runtime monitoring and controls available from the Noma AI agent security solution overlays real-time activity onto the Noma Agentic Risk Map using color-coding and dynamic visualization to show what’s actually happening across your agent ecosystem.
The platform continuously monitors prompts, responses, tool calling, and data flows to detect critical security events as they occur:
- Indirect prompt injections where malicious instructions are embedded in data sources
- Tool abuse where agents use capabilities outside their intended scope
- Risky actions that could cause data loss or system damage
- Data leakage where sensitive information flows to unauthorized destinations
- Privilege escalation via multi agent systems and MCP servers
When threats are detected, the platform enables immediate response, from alerting security teams to automatically isolating compromised agents or revoking dangerous permissions.
Why This Approach Works
AI agents require a fundamentally different approach to security that accounts for their autonomy, interconnectedness, and potential for rapid destructive action across multiple systems.
The comprehensive Noma Agentic Risk Map provides a solution desperately needed by enterprise security teams that require complete visibility into their AI agent ecosystem, clear understanding of risk scenarios, and real-time detection and control of active threats. By combining deep discovery, intelligent posture analysis, and continuous runtime monitoring, organizations can finally secure their AI agent deployments without sacrificing the productivity and innovation that make agents so valuable. Request a demo to learn how the Noma Security platform can help you secure your AI agents.



