The Model Context Protocol (MCP) is the new standard for equipping AI agents with real-world capabilities, connecting them to the tools and data they need to execute. The problem? Developers are deploying local and remote MCP servers independently, bypassing security controls entirely. These shadow servers hand AI agents destructive permissions over critical systems, creating blast radius risks that traditional security tools can’t see or stop.
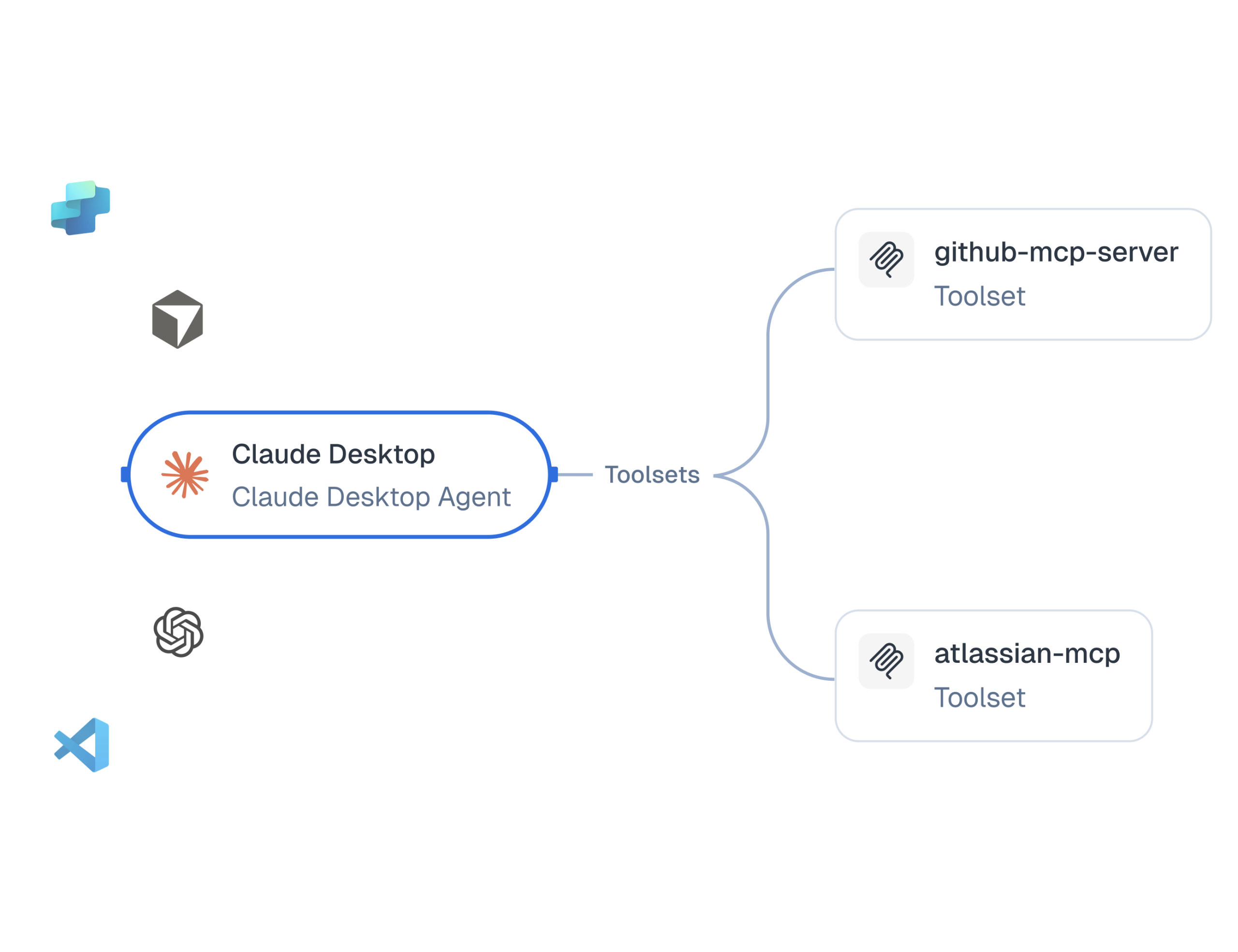
Noma MCP Security provides agentless discovery and protection across both sanctioned deployments and employee-driven shadow MCP use. Security teams see everything: which agents exist, what MCP tools they have access to, and what destructive capabilities they hold. Noma automatically surfaces risky configurations and maps potential catastrophic action paths across your entire environment.
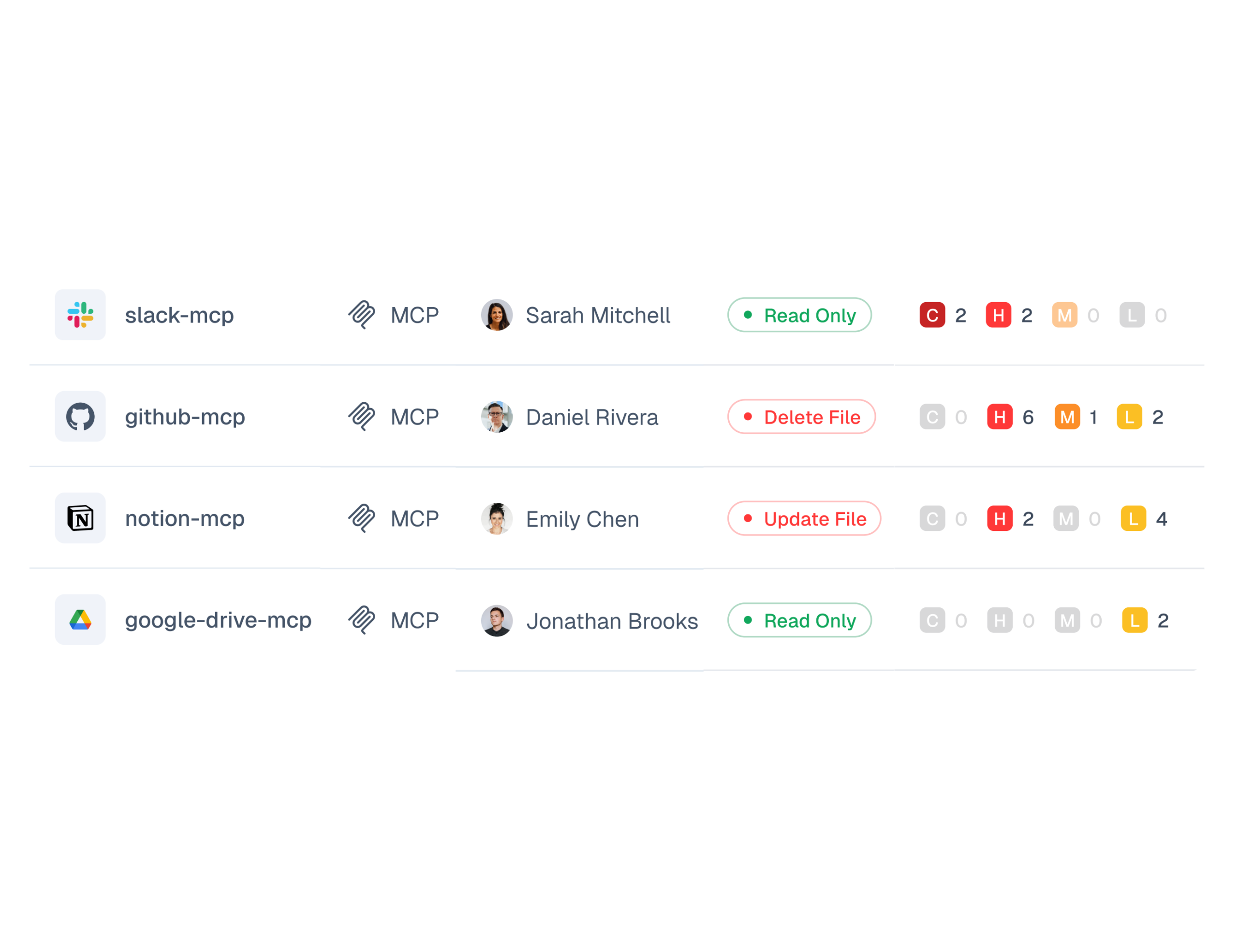
Instantly discover all MCP deployments and agent connections, whether deployed as part of sanctioned workflows or by employees directly. Visualize all access relationships and pinpoint situations where MCPs or agents may possess risky, excessive, or destructive capabilities.
Analyze the blast radius, excessive agency, and local asset compromise, identifying malicious supply chain servers while providing policies that can be implemented across all MCP connections to prevent credential leakage and destructive capabilities before they escalate to costly breaches or operational disruption.
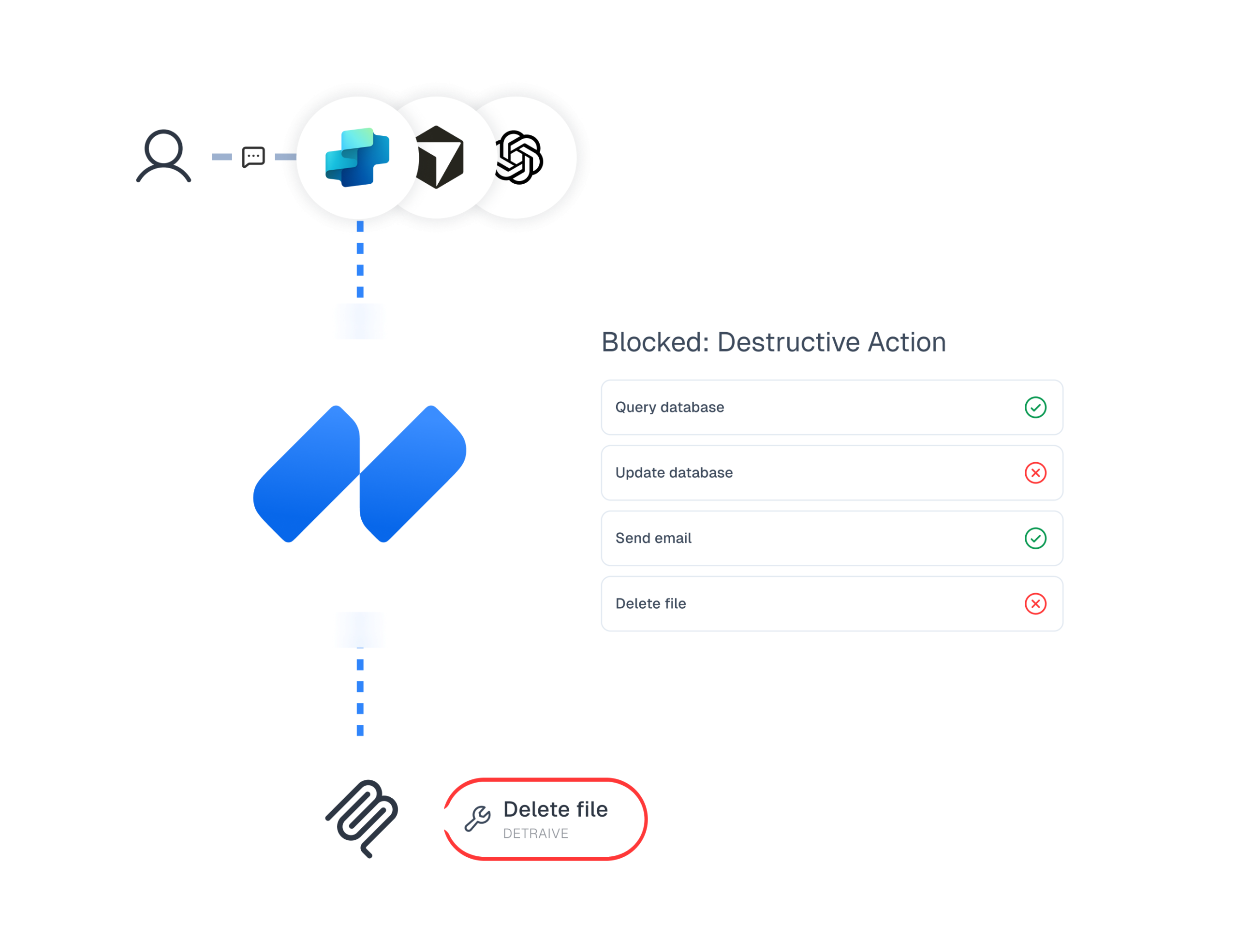
Define guardrails to restrict not only connections but agent permitted via MCP, blocking destructive actions, sensitive data leakage and enforcing least privilege access.
Enable responsible use of agentic workflows with MCP, keeping regulatory and audit requirements satisfied, and aligned to industry frameworks, ensuring that catastrophic action risks are always surfaced and addressed.

From development to runtime, proactively prepare your organization to meet emerging regulations and certifications such as the EU AI Act and ISO42001, with built in compliance that adapts to new requirements for AI as they emerge.

Align to AI Security frameworks including OWASP Top 10, MITRE Atlas and NIST RMF for seamless controls to secure critical data and AI models and protect against runtime threats such as prompt injection attempts, harmful content generation, sensitive data leakage and more.

Satisfy enterprise security requirements with built-in controls for data protection, access management, and threat detection to ensure your AI governance program meets SOC 2, ISO 27001, and other industry-specific security standards that auditors and customers demand.

Automatically generate an AIBOM to gain complete transparency and a deep understanding of your AI environment, including model provenance, licenses, and training data for full governance and adherence to compliance controls.

