53% of our Enterprise Customers Gave ClawdBot Privileged Access over the Weekend (And No One Asked Permission)
The viral AI agent that broke the internet is already inside most enterprise environments. Most security teams have no idea it is there.
A Weekend Phenomenon Becomes an Enterprise Risk
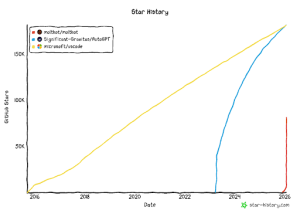
Last weekend, ClawdBot (now renamed as Moltbot) transitioned from a niche GitHub project to one of the fastest-growing AI tools in history. Between January 24 and January 27, it gained 54,000 GitHub stars. As of this writing, Clawdbot is at 82,000 stars and still climbing. Users are calling it the personal AI that Siri should have been.
The Allure of the “AI Employee”
The promise of a 24/7 AI employee that automatically manages your life and code is powerful. However, the current reality of ClawdBot is a security nightmare disguised as a productivity breakthrough. Our research reveals a landscape, fueled by agentic AI, where adoption speed has completely outpaced basic protections.
The Star Mirage
The most dangerous aspect of ClawdBot is its GitHub star count. This created a psychological trap for developers:
- Social Validation: Users see 82K stars and assume the project has undergone rigorous peer review.
- AI FOMO: The fear of falling behind drives users to run one-click install scripts without reading security warnings.
- The Amateur Influx: New hobbyists are treating this like a simple browser extension. They remain unaware that they are installing a remote access trojan (RAT) with an LLM interface.
Terminal Velocity: A New Benchmark for Danger
The speed of this adoption is unprecedented. While traditional tools built reputations over years, ClawdBot achieved “authority” status in hours.
What is ClawdBot?
ClawdBot is a locally run AI assistant that not only answers questions, but it also takes action on its own. It works directly on your computer, handling everyday digital tasks for you, from organizing files to interacting with websites and applications. Because it runs locally, it can access and do whatever the user can. ClawdBot takes instructions through familiar tools like Slack, Teams, or messaging apps, and it keeps working even when you’re not watching. Advertised as the ultimate digital helper, it claims to take work off your plate, so you can focus on decisions instead of busywork.
Why the Architecture is Inherently Destructive
ClawdBot is designed to be proactive, completely unbound by user identity. It does not wait for permission to act once enabled. It can autonomously fork repositories, make commits, and execute shell commands.
- Persistent Operations: Unlike GitHub Copilot, ClawdBot runs as a continuous background service. It stays active and reachable via WhatsApp, Microsoft Teams, Slack, and iMessage. An attacker can message the agent from a phone to execute commands on a workstation remotely.
- Unbound to any user identity: ClawdBot interacts with all users equally, regardless of their individual identity. In a Group Chat setting, the owner and other group members share the same access level, permissions, and ability to interact with the persistent memory and sensitive data.
- Autonomous Shell: ClawdBot executes arbitrary commands. A single prompt injection can trigger rm -rf / or exfiltrate environment variables.
- Localhost Trust: The system defaults to trusting localhost connections. When placed behind a reverse proxy, the entire internet looks like localhost to the bot.
- Credential Centralization: ClawdBot stores Anthropic keys, Slack OAuth tokens, and Signal pairing URIs in plain text.
- Root Access Misuse: Running the tool as root is a common mistake, which inadvertently grants the AI complete control over the host kernel.
What Noma’s Security Research Uncovered
As the industry began publicly sounding alarms, Noma’s AI security platform had already flagged ClawdBot instances across enterprise endpoints. Our research uncovered significant critical risks:
- Gateway and Control Plane Exposure The ClawdBot control plane manages configuration and tool invocation. We observed deployments where this plane was reachable beyond the local host due to misconfigured reverse proxies. Without authentication, this becomes a powerful remote control surface for arbitrary command execution.
- Dangerous Channel Policies ClawdBot receives instructions from external messaging platforms. We observed agents configured to accept messages from unrestricted populations. Untrusted users can trigger tool usage or cause the agent to access local data. Combined with browser automation, ClawdBot can perform end-to-end account takeovers by reading iMessage OTP codes.
- Sandbox Misconfiguration By default, ClawdBot tools execute on the host with the privileges of the user running the gateway. Any compromise leads to direct exposure. Even when users enable sandboxing, overly permissive workspace access or host mounts often erode that isolation and reintroduce risk.
- Plaintext Storage of Sensitive Data ClawdBot stores complete conversation history and all credentials in plaintext files with no encryption. These files commonly contain API keys and proprietary information. They remain accessible to any process with read access and are often included in unencrypted backups.
- Supply Chain and Extension Risks The ClawdHub skill registry allows users to install community skills with minimal vetting. Since these skills share core privileges, a malicious extension can exfiltrate data or establish persistence. Additionally, custom model provider configurations allow adversaries to redirect API calls through proxies to log sensitive data.
Why It Matters: The double “Lethal Trifecta”
ClawdBot epitomizes the “Shadow AI” crisis, a critical lack of visibility and control over personal AI agents operating on corporate infrastructure. Because traditional security tools fail to recognize AI-specific architectural patterns, these agents often bypass existing governance frameworks.
What makes ClawdBot uniquely dangerous isn’t any single vulnerability, but rather the sudden convergence of two distinct threat models:
For Sensitive Data Leakage:
The agent clearly breaks Meta’s Rule of Two :
- Processes untrusted inputs from any messaging platform sender, and any loaded context through tools, browser sessions, etc
- Accesses sensitive data, including credentials, files, integrations, and private conversations
- Takes external action via outbound messaging and network requests
For Destructive Actions:
ClawdBot is the definition of a destructive agent:
- Highly capable: Extensive integrations with destructive capabilities (shell execution, filesystem modification, browser automation)
- Highly autonomous: Operates as a background process with no mandatory human oversight
- Highly privileged: Executes with full user privileges and identity
How We’re Helping Customers Respond
When we identified active Clawdbot deployments, we moved quickly to help customers understand what was running, what it could access, and where risk existed. From there, we provided details to guide teams through hardening and put continuous monitoring in place to reduce the chance of misuse or compromise.
Discovery & Inventory: Complete visibility into where Clawdbot instances are running, how they’re configured, and what they can access.
Posture management: Automated analysis of the configuration of ClawdBot, including what it has access to, how it is deployed, what identity it embodies, and whether it has sufficient isolation
Guided Remediation: Step-by-step hardening guidance: isolating agents, preventing misconfiguration (e.g., binding gateways to localhost), enforcing authentication, and enforcing “least privilege principal”.
Ongoing Monitoring: Continuous detection of AI agent deployments and behavioral anomalies that could indicate prompt injection or misuse.
A New Architecture of Risk
ClawdBot is only the first wave. The next twelve months will bring an explosion of autonomous agents acting as personal assistants and workflow automators. Each brings a unique architecture and a new attack surface that traditional tools were never built to defend.
Don’t Wait for the Next Viral Hit
The time to secure your environment is before the next agent goes viral. If you do not know whether ClawdBot or the next major autonomous tool is already running on your network, you’re trying to secure what you can’t see.
Security must empower innovation, not obstruct it. Contact us today, and let Noma help you with the tools and research needed to see what is trending, identify risks, and manage and block them immediately.



